1 Introduction
1.1 The Need for Cybersecurity Transparency Audit
Cybersecurity is the practice of defending computers, servers, mobile devices, electronic systems, networks and data from malicious attacks. The role of cybersecurity is to ensure the protection of information and systems from major cyber threats.
Endpoint security and Endpoint protection are often used terms in the cybersecurity world because of the fact, it protects enterprises against unapproved access to data centers and other computerized systems.
Endpoint security in the Cybersecurity world has no standards. It is difficult for consumers to choose which Cybersecurity product because they have no way of knowing if these products follow certain standards or not. Cybersecurity is the only Multi Billion Dollar industry that has no standards yet affects our lives so much. Testing organizations are required to fill that gap.
1.1 Cybersecurity Transparency Audit Definiton
Cybersecurity Transparency Audit is an “Audit” program that testing organizations are auditing Cyber security vendors for their historical data.
1.2 About The Methodology
Testing Organizations plug into Cybersecurity vendors’ backend threat labs/collections/stats infrastructure with “some” extra work and permission and validate the results and issue Audit Certification.
1.3 Inclusion Criteria
Cybersecurity Transparency Audit welcomes the participation of any vendor who has minimum of 100,000 protected devices(endpoints). Testing organizations will require to apply to recommended policy settings; at least default or hardened.
2 Audit Test Components
Cybersecurity Transparency Audit testing requires large amount of data (from the endpoints that vendors protect) to be provided by vendors as follows:
2.1 File Information
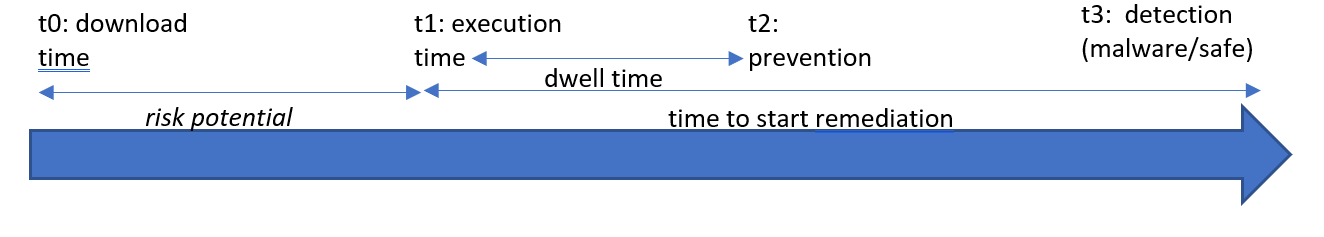
2.1.1 Time
- Dwell Time: time a file enters the system until classification (clean or malicious) must have
- Remediation Time: time from entry into the system (and classification as malicious) to remediation must have
- Average Remediation Time must have
- Local Detection Time must have
- Cloud Detection Time must have
2.1.2 Detection Statistics
- # of local detection & prevention must have
- % of local detection & prevention must have
- # of cloud detection must have
- % of cloud detection must have
2.1.3 Others
- # of unknown files that turned out to be clean must have
- # of samples unknown that turned out to be PUA/PUP must have
- # of unknown samples that turned out to be malware ("invisible threats" or "grey zone") must have
- # of detection by EDR or similar feature : whether AI, Heuristic, behaviour analysis or EDR must have
- malware with digital signature optional
- % of isolated(contained) unknown or malware files optional
- detect changes from previous quarter for file statistics ↑ ↓ optional
2.2 Device Information
- # of protected devices optional
- device vulnerability scanner / patch management : number of vulnerabilities detected | unpatched | patched optional
- system type : Windows % | Linux %| macOS % |... optional
- % of active devices with potential malicious activity (in Containment) optional
- # of cloud detection optional
- # of Cloud Query : Device count that send to Cloud Query optional
- # of Contained Malware Activity optional
- # of Malware Blocked at First Sight optional
- # of Operated in 100% Safe Posture optional
3 Audit Test Process
| Title | Categories |
|---|---|
| 1 | Cybersecurity vendor will provide an interface protected with credentials for only Testing Organizations access. |
| 2 |
Basic vendor data are required to be entered on that interface:
|
| 3 | Requested data for a specific time window should be provided to Testing Organization via that interface. This time window will be the start of the quarter and end of quarter for each audit period. |
| 4 | There should be Summary and Detailed display units on that interface based on Customer data, File data and Device data. There should be also filters for the values on these tables |
| 5 | Vendors will create a process whereby Testing Organizations will have access to this data any time they want to do an audit. The data needs to be updated on a regular basis, with a minimum daily pe |
| 6 | Vendor will provide the same data set via a programmatic API so that Testing Organization may plug into vendor’s backend threat labs/collections/stats infrastructure and fetch this data to their promises for further analysis. |
| 7 | The Testing Organization validated these results. The audit process is composed of a session with schedule agreed between vendor and testing organization. In this audit session, the testing organization and vendor work on the data provided for the audit period, and any further detail needed to clarify a case may be requested by testing organization, and the vendor provides answer to the testing organization using audit data or if needed internal data that has not been shared with testing organization yet. There may also be “spot checks” or questions being asked by testing organization on the data provided via the user interfaces |
| 8 |
Testing Organizations issue an Audit Test Report.
This report will consist;
|
| 9 | At the end Testing Organizations issue a Cybersecurity Transparency Audit Certification |